The defects named Meltdown and Spectre affect Windows 10 systems running on both Intel and AMD processors. Shared resource environments, such as virtual machines and containers running in cloud environments, are the most vulnerable to these exploits as one virtual machine could improperly access information from another.
However, if you are just using Windows 10 on a standalone PC, the threat of a Meltdown or Spectre attack is limited.
Here is how to manage the Meltdown and Spectre patches on your Windows 10 PC:
Install SpeculationControl Module
In January 2018, Microsoft released a PowerShell script to check if your PC is vulnerable to Meltdown and Spectre.
- Press Win+S and search for PowerShell. Right-click and select Run as administrator
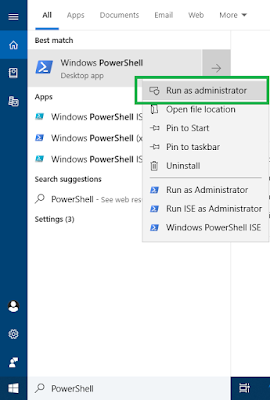 |
| Run PowerShell as Administrator |
- Check the current ExecutionPolicy to make sure PowerShell will allow you to run scripts
- Type Get-ExecutionPolicy and press Enter
- If it says "Restricted", then type Set-ExecutionPolicy RemoteSigned and press Enter
- PowerShell will ask for confirmation of the change. Type Y and press Enter
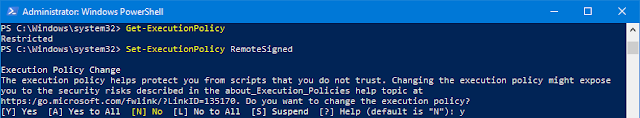 |
| Set-ExecutionPolicy RemoteSigned |
- Type Install-Module SpeculationControl and press Enter
- If a message says "NuGet provider is required to continue" type Y and press Enter
- Also type Y and press Enter for installing from an untrusted repository
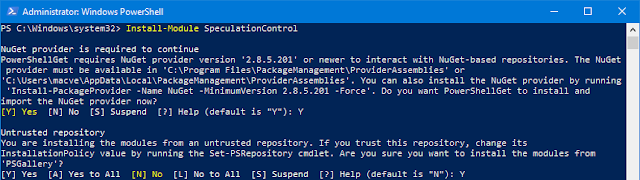 |
| Install-Module SpeculationControl |
- Type Import-Module SpeculationControl and press Enter
- Finally type Get-SpeculationControlSettings and press Enter
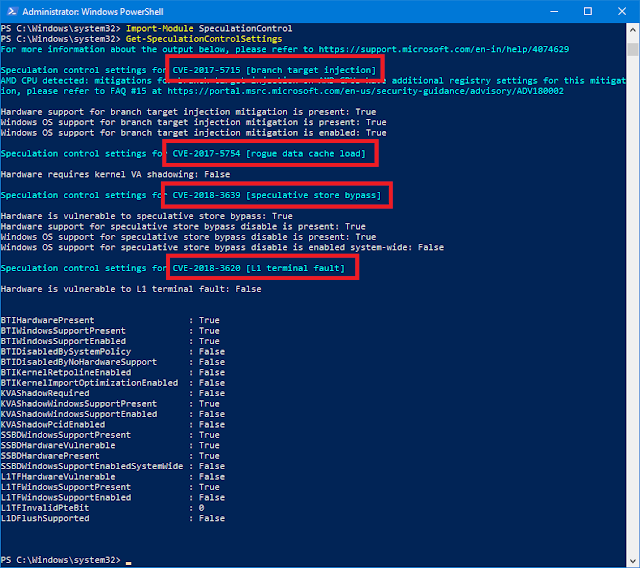 |
| Get-SpeculationControlSettings |
Vulnerabilities Summary
The following table addresses the Meltdown and Spectre vulnerabilities and which processors are affected by them:
| CVE |
Vulnerability Name |
Variant |
Affected Processors |
| CVE-2017-5753 |
Bounds check bypass |
Spectre Variant 1 |
AMD Intel |
| CVE-2017-5715 |
Branch target injection |
Spectre Variant 2 |
AMD Intel |
| CVE-2017-5754 |
Rogue data cache load |
Meltdown Variant 3 |
Intel |
| CVE-2018-3639 |
Speculative store bypass |
Spectre Variant 4 |
AMD Intel |
| CVE-2018-3620 |
L1 Terminal Fault |
Foreshadow |
Intel |
Disabling Mitigations
The mitigations for Meltdown and Spectre can cause real performance hits to Windows 10. Currently, it is only possible to disable
Spectre Variant 2 mitigations with a modification to the Windows 10 registry and a reboot.
WARNING: Disabling mitigations makes your system less secure and more vulnerable to attack
Disable Spectre Variant 2 Mitigations
- Press Win+S and search for Command Prompt. Right-click and select Run as administrator
- Execute the following commands:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 1 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
- Reboot for the registry settings to take effect
References





Comments
Post a Comment